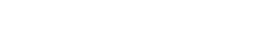Digital transformation: Building cyber resilience in the oil and gas industry
The oil and gas industry is boosting cybersecurity spending, as heightened geopolitical tensions and the accelerating adoption of digitally connected infrastructure spark concerns over vulnerabilities to emerging cyber threats. This is according to DNV’s Cyber Priority research exploring the changing attitudes and approaches to cybersecurity, in the energy and maritime sectors.
A majority (62%) of oil and gas professionals surveyed by DNV for the research say their organization has been investing more in cybersecurity during 2023, compared with last year, acknowledging that cyber-attacks on the industry are a question of “when,” not “if.” Asset owners and operators have been tackling IT security for decades but securing operational technology (OT)—the control systems that manage, monitor, automate and control industrial operations—is an increasingly urgent challenge.
Only half (52%) of oil and gas professionals believe their company is investing enough in building up the cyber resilience of operational assets and infrastructure. While this is higher than for the power and renewables sector (47%) and companies providing services across the energy industry (38%), it still leaves around half of energy professionals believing their organization needs to invest more, Fig. 1.
The industry is deeply dependent on systems that are becoming more digitally connected to bring down costs, increase efficiency and decarbonize the sector. Nine in 10 (91%) oil and gas professionals believe cybersecurity is a pre-requisite for the digital transformation initiatives that are making the future of the energy industry possible.
The energy industry cannot reap the benefits of digital transformation without robust cybersecurity. Two thirds (69%) of oil and gas professionals worry that their organization is more vulnerable to cyber-attacks on their OT networks now than at any other point in their history.
GEOPOLITICS INCREASING AWARENESS OF CYBER SECURITY RISKS
Russia’s invasion of Ukraine—and related cyber-attacks—continues to send shockwaves through the energy sector. Attacks on OT materialized soon after the start of the invasion against the energy sector.
Some 79% of oil and gas professionals say geopolitical uncertainty has made their organization more aware of the potential vulnerabilities in its operational technology. And two-thirds (69%) say that their organization’s focus on cybersecurity has intensified as a result of geopolitical tensions.
More broadly, recent geopolitical developments have brought energy security—not just cybersecurity—into sharp focus, with the disruption of energy supplies and price shocks for energy importers. For the first time in DNV’s power sector forecasts, for example, we now factor in the willingness of governments to pay a premium of between 6% and 15% for locally sourced energy, to ensure security. Security is high on the agenda in the energy transition, and cybersecurity has a major role to play.
STATE ACTORS AND HACKTIVISTS SEEN AS A MAJOR THREAT
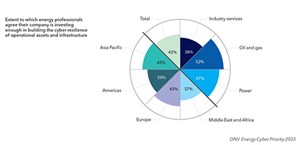
Our research shows how the profile of cyber-attackers in the energy industry has changed since early 2022. In the immediate aftermath of Russia’s invasion of Ukraine, we saw an increase in the perceived threat posed by all forms of threat actors, in the two weeks following the invasion in February 2022. In the year since, energy executives remain highly attuned to the threat created by the Ukraine war—either by politically-driven hacktivists or by hostile states—but they appear to have returned to pre-invasion levels of concern about longer-term adversaries, such as criminal gangs and malicious insiders, Fig. 2.
Attacks on OT are likely to be instigated by state actors. And outside of open conflicts, like in Ukraine, these attacks are largely designed with the aim of making noise and a statement about their capabilities and means, rather than unleashing full major incidents. We should not forget insider threats and physical sabotage, and the oil and gas industry should continue to take an integral approach to security—including both cyber and physical. The good news is that the industry has good experience in ensuring physical security.
Hacktivists, often focused on environmental concerns, are looking to create disruption and send a message—not to cause major incidents that could pose risks to life and the environment. OT is interesting for financially motivated cyber criminals, but maturity-wise, it’s not so easy to hack into these OT systems from the outside; it is often on the IT side that attacks take place. This was the case with the cyber-attack of Colonial Pipeline in 2021, which resulted in major disruption to the flow of oil in the U.S.
VULNERABILITIES IN THE SUPPLY CHAIN
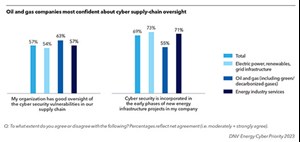
Oil and gas professionals rank inadequate oversight of the vulnerabilities of supply chain partners connected to their organization’s environment as the greatest challenge in enhancing OT cybersecurity. This is followed by the challenge of projects to strengthen cybersecurity disrupting ongoing operations, which reflects the reality that in industries like oil and gas, the situation is one in which one needs to repair and upgrade the car while driving it.
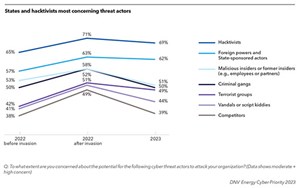
Just 57% of professionals across the energy industry say that their organization has good oversight of the cybersecurity vulnerabilities in their supply chains. Indeed, each year, a huge number of vulnerabilities are discovered in products. Supply chain is on the top of the agenda for the industry, but it is not easy to fix. Measures supporting third-party assessment are improving the situation, but there remains much more work to do.
Perhaps the most proactive approach is security by design, which places cyber security at the centre of new projects. We’ve been talking about this approach for the last 10 years, but it is slow to gain ground. It’s a question of maturity; think about car manufacturers trying to sell vehicles without seatbelts, to avoid carrying the extra costs. Regulation wouldn’t allow it. Security should always be the standard, and the oil and gas industry is moving in this direction with cybersecurity, albeit slowly, Fig. 3.
GROWING APPRECIATION OF BUSINESS AND SAFETY RISKS
Evolving cyber risks and greater awareness of them help to explain why more than six in 10 oil and gas professionals say that cybersecurity has become a regular fixture on their organization’s boardroom agenda, and three-quarters of oil and gas professionals report that cybersecurity is treated as a business risk within their organizations. Tightening regulation is playing a role, with a trend for regulation globally to assign management responsibility for cybersecurity within organizations—particularly for organizations operating critical infrastructure, which includes oil and gas.
With growing awareness of the cyber threat, it should, perhaps, be no surprise that threequarters (75%) of oil and gas professionals say they take cybersecurity as seriously as they do physical health and safety. Any evidence that the industry is ramping up its security posture is welcome, but more work is required for oil and gas companies to be able to confidently say they treat cybersecurity as seriously as safety.
Compare growing awareness of cyber risk with the change in mindset around safety standards that took place in oil and gas during the late 20th century. Oil and gas operators at the time took an inconsistent approach to health and safety, until incidents like Piper Alpha and Seacrest forced leaders to adopt standard protocols.
The C-suite and boards of directors face increasing accountability and responsibility for managing cyber risks and are acting accordingly. But organizational efforts must reach endusers and engineers on the front line. Training and putting security controls in place is vital.
CONSTRAINT DETERMINATION TO BUILD RESILIENCE
Most oil and gas companies look at five areas of risk related to cyber-attacks: financial, reputational, impact on people and safety, damage to assets, and effects on the environment. Every day that goes by without incidents, and these risks being realized, is a day that these companies see cybersecurity contributing to their operational excellence. If there is no impact and everything is running smoothly, then their cyber resilience efforts are paying off.
Attacks happen every day, and while criminals are enjoying success with easy targets, they are finding it increasingly difficult to target companies that are doing things by the book and working hard on their defenses. Security is improving overall, but the work never stops; there are always emerging threats to manage.
To build resilience, oil and gas companies need to understand how an attack can impact on their operations and primary business processes. Could an incident see production shutdown? Could it impact the delivery and agreements the organization has with customers, clients and partners? Could it have an impact on the public and see critical infrastructure that provides gas to a country shut down?
Companies need to have plans in place and know how quickly they can recover. These incidents will happen, and an indication of cyber resilience is the speed of the recovery process to resume operations.
Oil and gas companies need to constantly raise their standards. They must ask themselves whether they are learning and whether they are doing the right things. This internal scrutiny can be a source of confidence for companies. Encouragingly, energy companies are increasingly seeing cybersecurity as a business enabler.
TIGHTENING REGULATION TO INCREASE CYBER RESILIENCE

Regulatory requirements are the foremost driver of investment in cybersecurity within the oil and gas sector and the wider energy industry. Almost half (49%) of energy professionals say that changing regulatory requirements is one of the factors most likely to unlock increased budget, with the next nearest catalyst being a cyber incident (or near miss), as cited by 38%, Fig. 4.
In the EU, for example, organizations providing essential services—including many in the energy sector—face tougher regulation in the form of the revised Directive on Security of Network and Information Systems (NIS2), set to be transposed into national laws in 2024. As well as widening the scope of organizations covered by regulation, the directive increases the required standards of executive oversight and imposes new reporting charges. Penalties for non-compliance have increased to €10 million or 2% of a company’s global annual turnover, whichever is higher.
In the U.S., the Department of Energy is continuing to work on the National Cyber-Informed Engineering Strategy, and there is focus—including an executive order—on driving vendors to provide a software bill of materials, which itemizes the components in software and enables better third-party assurance.
NEW TECHNOLOGIES SET TO CHANGE THE GAME
New and emerging technology will have a major impact on cybersecurity. But what can be used for good can also be used for bad.
AI, for example, is making it easier for attackers to automate, and it is supporting their ability to carry out large-scale attacks. If quantum computing gets into the hands of bad actors, they will be able to overcome current cryptography and crack any code. The Cloud is also interesting, as data and OT connections are migrated to the Cloud, and discussions are ongoing between vendors and operators about who is responsible and what actions should be taken to secure data.
On the other hand, AI and quantum computing will help on the defensive side, enhancing detection and response capabilities.
PREPARING FOR THE INEVITABLE
Oil and gas companies need to know their assets, including what they’re connected to, what technologies they are using and what must be protected. Attack surfaces can be wide, and focusing on the basics is a good place to start when ensuring that you’re not an easy target.
When evaluating their cyber posture, oil and gas companies should consider how they are measuring the strength of their defenses and recovery plans, how they are benchmarking performance, and whether they have identified the improvements they need to make. It’s only once they have systematically outlined the gaps in their defenses that they can put plans in place to close them.
Ultimately, there must be a consistent effort to ensure cyber awareness and appropriate action at every level of an organization—from C-suite to operational roles—to ensure a cohesive approach to safeguarding operations. That way, asset owners and operators can strengthen their cybersecurity posture and build resilience against the ever-evolving threats in an increasingly connected and targeted sector.
A proactive approach to cybersecurity can also drive competitive advantage. By being at the forefront, oil and gas companies can continue to define excellence, meet and exceed new standards and elevate best practices.
Because ultimately, if an incident hasn’t happened already, then it could tomorrow, and the one thing businesses have absolute control over is how ready they are to deal with it.

- Aramco's upstream digital transformation helps illuminate the path toward excellence (June 2024)
- Adopting a holistic approach to cybersecurity (March 2024)
- Embracing automation: Oil and gas operators leverage new operational efficiencies (May 2024)
- The five A’s on the road to completions automation (May 2024)
- Digital’s influence on drilling and production keeps growing (March 2024)
- Taming the red zone with automation (April 2024)